Earthmasters?
Thursday, June 20th, 2013Earthmasters, The Dawn of the Age of Climate Engineering, Clive Hamilton, 2013
The title of this book is intended ironically. We are masters of the Earth only in the sense that we have the power to destroy all life forms on Earth but lack the will or the knowledge to prevent that destruction. 350.org was named for the number of parts per million of carbon dioxide in the atmosphere that scientists believe to be the tipping point beyond which catastrophic climate changes are inevitable. We are currently at 395 parts per million and climbing with predictions of 700 or even 1100 by the end of this century. In other words, carbon dioxide in the atmosphere must be reduced, not merely stabilized to avoid the inevitable catastrophe. Hamilton summarizes:
It took the Earth millions of years to immobilize a large portion of the planet’s carbon in fossilized form deep underground. When we extract and burn it we mobilize the carbon and there is no place on Earth where, over human timescales, we can safely sequester it again. We know we cannot leave it in the atmosphere, Carbon stored in vegetation and soils is always on the brink of release through fire or human disturbance. The oceans are in constant flux, with even the deepest layers naturally coming to the surface sooner or later. Heavily promoted plans for carbon capture and storage, in which carbon dioxide extracted from the smoke-stacks of coal fired power plants is pumped in geological repositories underground, looks increasingly risky and expensive. I hope we have learned enough by now to be wary of any technology that claims to have found a way to immobilize for centuries huge quantities of carbon somewhere in the Earth system where it does not belong. Even if such a place could be found there is something deeply perverse in the demand that we construct an immense industrial infrastructure in order to deal with the carbon emissions from another immense infrastructure, when we could stop burning fossil fuels.
When you are already in a hole, stop digging. That would be too sensible.
Hamilton discusses a group of climate engineering suggestions intended to regulate sunlight including making clouds whiter or generating more or fewer clouds in various parts of the world. The main focus of research, however, seems to have been on studying the effects of the historic volcanic eruptions of Laki in 1783 (effects studied by Ben Franklin), 1816 (the largest in recent history and resulting in famines), Krakatoa in 1883 and Pinatubo in 1991. All resulted in significant cooling of the global climate. Hamilton, tongue in cheek, notes that Krakatoa inspired “Frankenstein“, Lord Bryon’s poem Darkness, and Edward Munch’s painting “The Scream“.
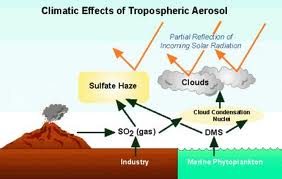
The climate engineering idea is to somehow put sulphate aerosol particles into the stratosphere which is between 10 and 50 kilometers in altitiude. The engineering problem is getting the quantity of particulars required up there. One estimate has thousands of special planes making a million flights per year to produce the equivalent effect of the 1991 Pinatubo eruption. The big problem for researchers is that it is difficult to learn much from small scale experimentation and full scale deployment will undoubtedly have unforeseen consequences. Scientists agree that it would cool the Earth. Some believe more limited deployment over the arctic could reverse the melting of the ice and cool the Earth sufficiently. There is major concern that the sulphates would further damage the ozone layer, delaying its recovery for decades and increasing the ozone holes. The effects on patterns of rainfall and monsoons is unknown but likely large.
Then there is the problem that once started it would be impossible to stop the program regardless of the political or economic climate. Stopping it in the future would lead to instant warming without giving life on Earth any time at all to adapt. The catastrophe would be immediate and worse than if the program had not been started in the first place. This plan would affect everyone on Earth but the decision to go ahead could be made by a single nation or even a single very wealthy individual. Billions of people would be put at risk without having any say in the program.
China and India live within a constant brown haze from industrial emissions pollution that cause more than a million deaths a year. The US and Europe have put emissions controls in place to greatly reduce the pollution and China and India want to do the same. The problem is that reducing the haze results in increased warming so you trade improved health for accelerated climate change. There is little doubt that both countries will implement their emissions controls programs.
Caldeira liming the oceans 
Keith let’s buy an ice age 
Research in geoengineering is controlled by a small, incestuous group where two scientists, Ken Caldeira and David Keith, are so dominant they have been labeled the “geoclique“. Bill Gates is the biggest backer, but funds are also provided by N Murray Edwards, a Canadian oil billionaire with an enormous stake in the oil sands. Hamilton likens this to cancer research being funded by big tobacco. Keith plans to “test” sulphate aerosol spraying in New Mexico. Caldeira is conducting small scale tests of liming the oceans. Hamilton is worried that the backers, which include Richard Branson, are engaged in magical thinking, looking for the sexy “killer application“. They view existing technologies for wind and solar energy, insulation, and other energy reduction methods as boring and old fashioned, definitely not sexy.
Gates  Branson
Branson  Magical Thinkers
Magical Thinkers
The geoclique has its origins, not surprisingly, at Lawrence Livermore Labs, home of nuclear Armageddon. The Dr. Strangeloves of geoengineering suggest we simply move the Earth a little further from the Sun perhaps by detonating a huge nuclear blast to steer a large asteroid close to the Earth. Hope they don’t miscalculate!
BP, Shell, and Exxon are all investing in geoengineering. Hamilton notes that the melting of arctic ice has made previously protected reserves of oil that were under the ice now accessible. The arctic oil gold rush is on so don’t expect an arctic sulphate aerosol shield anytime soon.
Big oil seem to favor experiments to get the ocean to absorb more carbon dioxide from the atmosphere by stimulating the growth of carbon eating lifeforms by fertilizing the oceans with iron or liming. The oceans are very complicated and the effects of major deployment are unknown. Major deployment would require massive industrial infrastructures and would divert chemicals needed to grow food. Phosphorous, in particular, is a scarce resource that should be preserved for food growing. Simply outlawing the killing of whales could have a big effect on the ability of the oceans to absorb carbon but the chances of passing such laws are negligible. Big oil is also supporting very small scale experiments in algae and other plants as “carbon neutral” sources of energy. This is safe for big oil since land, fertilizer, and water are not available for growing the plants on a meaningful large scale.
Hamilton notes the bizarre and illogical willingness of climate change deniers to embrace geoengineering technofixes to a problem they deny even exits:
..if planning to take control of the Earth’s climate system forever – using highly speculative technologies and risks – is needed to appease those whose prejudices prevent them from accepting scientific fact, then that is what we must do…We know we are in trouble when liberals who say they accept the science begin advocating geoengineering as a means of appeasing conservatives who reject the science.
This new coalition, in the name of doing something politically, is likely to embrace grand system changing interventions like stratospheric sulphate aerosols rather than more modest efforts like reforestation, biochar, or painting roofs white, and to favor US unilateral implementation of those grand schemes.
More humble scientist Ron Prinn asks: “How can you engineer a system you don’t understand?” Overconfident geoengineers say we just need to decide where to set the thermostat.
The Earth’s decision makers lost an entire decade waiting for the miracle of Carbon Capture and Sequestration (CCS) in which carbon was to be extracted from the smoke chimneys of coal fired plants and permanently stored somewhere. The oxymoron “clean coal” CCS was never technically or economically feasible. We are now well into the second decade of waiting for the magic solution that won’t require changes to the existing social and political power structures or our life styles.
This time, the magic solution seems to be stratospheric sulfate aerosols made public for the first time in a 2006 “intervention” by Dutch scientist Paul Crutzen with his essay “Albedo (Reflection) enhancement by stratospheric sulfur injections: A contribution to resolve a policy dilemma?” Crutzen strongly believes that we must also find ways to reduce carbon emissions as well as ways to remove carbon from the atmosphere, but not all sulfate aerosol advocates share this conviction. Many seriously believe we can carry on as usual to burn fossil fuels, compensating for the resulting climate changes with sulfate aerosols or ocean cloud whitening. This is just what those that control big oil and coal want to hear. Little attention is given to “side effects” like damage to the ozone layer and changes to weather patterns affecting monsoons and inducing droughts.

Lonnie Thompson stores a million year history of Earth’s Climate gathered from the highest places on the planet
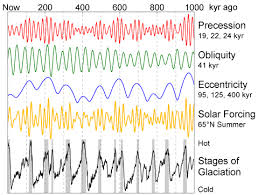
A previous post Thin Ice discusses the three cycles of Earth orbit and wobble which, in the past, have determined patterns of Earth temperatures with long ice ages followed by short warm ages. The last 10,000 years, during which time agriculture and human civilizations have risen, has been named the “Holocene”. In 2000, Crutzen and another scientist declared a new age, the “Anthropocene”, the age induced by human activity.
With the Anhropocene, humans have become a geological force, so that the two kinds of history have merged…Our future has become entangled with that of the Earth’s geological evolution. Anthropogenic climate change affects not just the atmosphere but the chemical composition of the oceans (acidification), the biosphere (species extinctions and shifting habitats), the cryosphere (melting ice masses), and the lithosphere itself.
Yet how can we think our way out of the problem when the problem is the way we think? There is something increasingly desperate about placing more faith in technological cleverness when it is the unrelenting desire to command the natural world that has brought us to this point.
The magnitude of this climate change is emphasized when we realize the already released carbon dioxide from burning fossil fuels will suppress the entire next ice age. Brace yourselves for the geoengineering era. Geoengineers are “Earthmasters” like Wall Street denizens are “Masters of the Universe“. Maybe they can hold a competition to see who can do the most damage.