High Price of Investigative Journalism
Saturday, December 13th, 2014Pay Any Price; Greed, Power, and Endless War, James Risen, 2014
Risen gives an eloquent rational for writing this book:
In 2009, when the new Obama administration continued the government’s legal campaign against me, I realized, in a very personal way, that the war on terror had become a bipartisan enterprise. America was now locked into an endless war and unintended consequences were spreading. And so my answer — both to the government’s long campaign against me and to this endless war — is this new book, Pay Any Price. Pay Any Price is my answer to how best to challenge the government’s draconian efforts to crack down on aggressive investigative reporting and suppress the truth in the name of endless war. My answer is to keep writing, because I believe that if journalists ever stop uncovering abuses of power, and ever stop publishing stories about those abuses, we will lose our democracy.
Paul Bremer, Mastermind of Chaos 
The book itself seems to have been written or at least published backward with the vaguest and weirdest stuff put first. In 2003 and 2004 $20 Billion in $100 bills was air lifted by military transport to Iraq. Serial numbers were not recorded and there was virtually no supervision or safeguards. Most of the money simply disappeared. Risen reports of one shipment of $1.6 Billion sent to a branch of the Iraq Central Bank in northern Iraq and stacked on the floor of the bank – not in a vault. The money vanished. When $1.6 Billion was reported found in a bunker in Lebanon, the US government couldn’t even be bothered to investigate under either W or Obama. Overall the US spent $63 Billion on the reconstruction of Iraq, most of it going to US contractors. Many is not most of the contracts were never completed and some were never even started.
Risen then turns to fraudsters of the war on terror, featuring Dennis Montgomery who used phantom-ware to decode secret Al Quaeda messages hidden in Al Jazerra broadcasts. His reports caused the grounding of international flights and a serious discussion of shooting down commercial airliners. When he approached the French government, their experts quickly exposed the hoax. The US government, having been duped, buried the incident under a mountain of top secret documents.
He features the Blue’s brothers who bought an unmanned aircraft subsidiary, General Atomics, for $50 million and now have a privately held near monopoly on US war drones.
He turns to to KBR the former subsidiary of Halliburton (Dick Cheney CEO), the military’s largest contractor. KBR built substandard housing for US troops using indentured third world untrained labor and with poor or nonexistent supervision and inspections. The result were showers that electrocuted soldiers. One mother persisted in finding out how her son died and then sued KBR. She won on appeal and the case has been appealed by KBR to the supreme court. Risen calls this section Too Big to Fail but it is really Too Big to Jail as with the banks who can’t even get prosecuted for massive drug money laundering activity. The shower electrocutions pail in comparison to the damage caused by KBR’s practice of burning trash (several hundreds of tons per day) in open pits using jet fuel. KBR burned anything including computers, batteries, and other electronics. This has led to the discovery of “war lung injury” this war’s equivalent of Agent Orange in Vietnam and Gulf War syndrome from exposure to uranium shells in the first Gulf war. Returning soldiers were found with titanium and unusual bio masses in their lungs as a result of exposure to the burning pits. The VA and DOD have gone to great lengths to cover up the problem and have failed to survey returning soldiers, provide diagnosis and care, or even to acknowledge a problem. One VA researcher Stephen Coughlin uncovered some suppressed studies and went to Congress with his findings. He was forced to resign under enormous pressure. One DOD official, Charles Smith, stood up to KBR when auditors pointed out a $1 Billion overcharge. He proposed opening bidding to other contractors. Smith was sidelined and soon retired.
Risen talks about the prison torture and abuse scandals and the “few bad apples” campaign by the government to scapegoat low level guards. When one prosecution failed, the government abandoned its efforts at scapegoating but the whole prison guard experience ruined many lives. Risen focuses on the the role of psychologists and the APA who gave cover to the torture program. The APA used the old NAZI argument that if the activity was legal (according to W administration legal justifications) it must be ethical. The DOD and VA are the largest employers of psychologists and their careers and livelihoods depend on giving the government what it wants. The legal rational is based on the military use of the techniques in training, particularly the SERE navy training. Risen shows what nonsense the use of torture is by presenting the navy SERE’s own PowerPoint presentation:
Why is torture the worst interrogation method?
Produces unreliable information
Negative world opinion
Subject to war crimes trials
Used as a tool for compliance
Brennan Defends Torture Dec 12, 2014 
Yesterday, CIA director Brennan once again asserted that actionable intelligence was gained from the use of torture and it shouldn’t be banned outright. Utter nonsense as Diane Feinstein rebutted him point by point. Obama refuses to pursue war crimes prosecutions.
Haskell Free Library and Opera House Canadian Border Line 
Risen turns to the cost of the endless war on ordinary American citizens. Most obvious are airports that today resemble high security prisons that visitors must transit if they want to fly. He features two small towns on the border, one in Vermont and one in Quebec that built an opera house spanning the border. The house, with its painted black line is the main tourist attraction of the towns. For generations residents have freely traveled back and forth across the border to shop and visit. Most residents didn’t even own passports since few travel abroad. All this changed after 9/11 when abusive homeland security outsiders started arriving in town. They build a fence and closed off all roads but one which is heavily guarded. Residents now require expensive passports and must endure abusive officials as they cross. When the local pharmacist was arrested for walking two blocks to pick up a pizza in Canada public outrage forced the reassignment of the homeland security official in charge. The draconian treatment eased but the fence and closed streets remain and passports are now required.
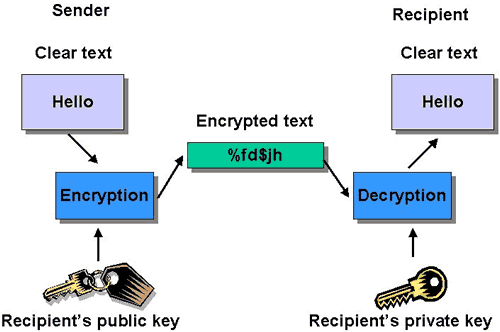
Risen turns to the story closest to him, NSA warrant less surveillance and gives the best account yet of all the insiders who attempted to blow the whistle on the illegal activity. The efforts cost each of them their jobs and the government has ruined many lives. Featured here is the little known story of Diane Roark, a staffer for the House Permanent Select Committee on Intelligence. Her personal battle with NSA Director Michael Hayden dates from 2000 prior to 9/11 and the war on terror. It starts when NSA’s Bill Binney discovers that a part of the program he had worked on was being misused with the built in protections against spying on Americans removed. When his internal efforts to stop the activity failed, Binney reached out the Roark who immediately recognized the illegality of the collections. Roark quickly discovered her contacts inside the NSA and the house had been secretly informed of the program and none were objecting. When Roark contacted the Chief Judge of the FISA court Coleen Kollar Kotelly, Kotelly not only did not respond but she notified the Justice Department to inform them Roark was asking questions. Roark was forced to resign but this was not enough for Hayden who insisted on meeting Roark in person. Roark took notes and these are a summary:
General Michael Hayden Repeatedly Lies to Congress 
I (Roark) pushed hard and repeatedly about why he had dropped the protections (for American Citizens). He avoided answering until finally he said again that they didn’t need them because they had the power.
Wyden Silenced by Classified Disclosures 
Roark was stunned by this answer. The rest of the conversation was equally shocking. Hayden believed that seeking authorization would shed unwanted light on the program. That “It is now among us.” I.E. the program is permanent and expanding. He told her he believed he would prevail if the program came before the supreme court and that he was considering leaking it to select Congress members to assure their silence. Among those silenced appears to be Oregon Senator Ron Wyden. Hayden was telling Roark all this to warn her to drop her efforts to oppose the program. Still, Roark took a chance and wrote a letter to Supreme Court Chief Justice William Rehnquist via hand delivery from Rehnquist’s daughter. Rehnquist never responded. The FBI sent a phalanx of officers to Roark’s Oregon home to seize all her files, computers, etc. Her lawyer advised her to ask for the affidavit in support of the search warrant and the FBI responded it was under seal and she couldn’t see it. That same day the FBI raided the homes of three other NSA whistle blowers. A few months later they raided the home of NSA whistle blower Thomas Drake. This time the supporting affidavit was later discovered to indicate the FBI was looking for evidence that Drake was the source of the leaks to reporters James Risen and Eric Lichtblau. The NYT repeatedly killed the NSA story for two years from 2004 til 2006 when they published it just weeks before the release of Risen’s book State of War. So much for the newspaper of record.
Risen comments that he fully understands why Edward Snowden felt compelled to leave the country before blowing the whistle on the NSA given the devastating personal experience of all previous NSA whistle blowers. In 2005 Risen reported on a botched harebrained CIA plan to give nuclear weapons blueprints to Iran. The government is still after Risen to reveal his source for this story and Risen faces jail time if he refuses to cooperate. The only way to go to jail in this country today is to be poor or to be an investigative reporter. Pretty sad.